AWS released a new feature of SSM Systems Manager on September 11th, 2018. This new feature allows organizations to control access to the EC2 instances using a secure manner. Some of the top features are:
- Fine-tuned granular control to instances using IAM policies
- Support for tags, users, instance IDs, etc
- Uses existing Amazon SSM Agent installed on your instances
- Minimum supported version is 2.3.5
- No need for SSH key pairs or SSH ports
- Two factor authentication support when logging into the AWS console
- Encrypted auditing and logging of sessions
- Each session is logged in a separate log stream in a log group or S3 bucket
- Support for CloudTrail, CloudWatch Events, SNS, etc
- Support for both Windows and Linux
As you can see this is a huge feature. Many enterprises are struggling to control access to their systems with two factor authentication support and session recording. It's a tremendous pain point for many security and systems administrators. Luckily within Amazon's ecosystem this is solved easily using SSM Systems Manager Session Manager and a little bit of IAM.
SSM Agent Support
To get started with Session Manager, add an IAM policy to your instance to support connectivity to the SSM Systems Manager. You may use the AmazonEC2RoleforSSM policy that Amazon packaged for us. Attach it to your instance-profile role.
You can also add an inline policy to your existing IAM policies if you don't like adding AWS-managed policies. Below policy is the absolute minimum to setup Session Manager. Please note that you will need additional statements permitting access to the rest of SSM Systems Manager.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ssmmessages:CreateControlChannel",
"ssmmessages:CreateDataChannel",
"ssmmessages:OpenControlChannel",
"ssmmessages:OpenDataChannel"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"s3:GetEncryptionConfiguration"
],
"Resource": "*"
}
]
}
You will also need the SSM agent installed on your instance. You can do so via:
$ yum install https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/latest/linux_amd64/amazon-ssm-agent.rpm
$ systemctl enable amazon-ssm-agent && systemctl start amazon-ssm-agent
You should now be able to launch a session to the instance. Follow on to configure logging.
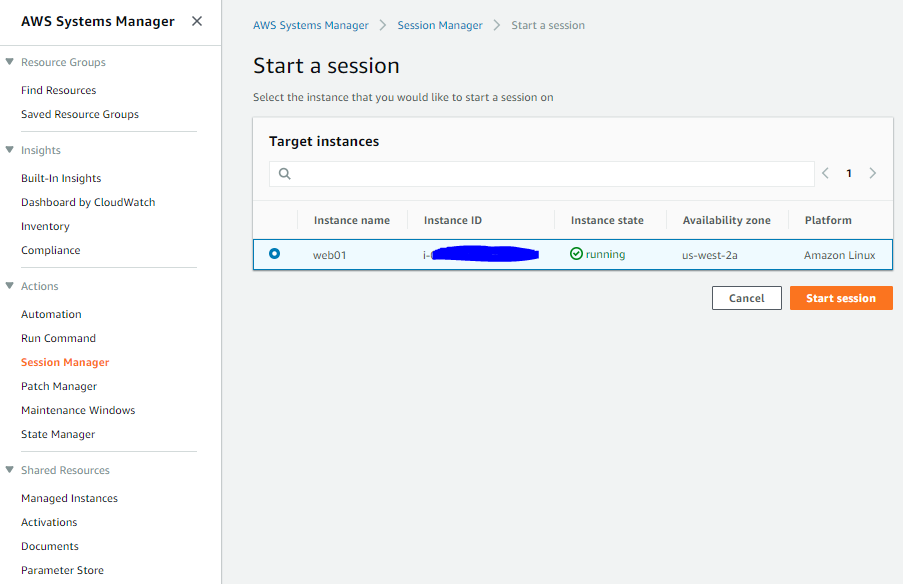
Start a Session

Actual session
Ability to launch sessions can be limited by implementing IAM policies for your users or roles. Sample policy below would limit access to only web servers:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ssm:StartSession"
],
"Resource": [
"arn:aws:ec2:*:*:instance/*"
],
"Condition": {
"StringLike": {
"ssm:resourceTag/ServerRole": [
"WebServers"
]
}
}
},
"Effect": "Allow",
"Action": [
"ssm:TerminateSession"
],
"Resource": [
"arn:aws:ssm:::session/${aws:username}-*"
]
]
}
Encrypted CloudWatch Logs
In order to encrypt your CloudWatch logs, you will need to create a Log Group and specify a KMS key ID. This has to be done through CLI as it's not yet supported in the CLoudWatch console. Also remember to add the CloudWatch Logs service to your KMS key policy:
$ aws logs create-log-group --kms-key-id arn:aws:kms:us-east-1:${AWS::ACCOUNT}:key/${KEY_ID} --log-group-name session-logs
Configure logging as per below screenshot.
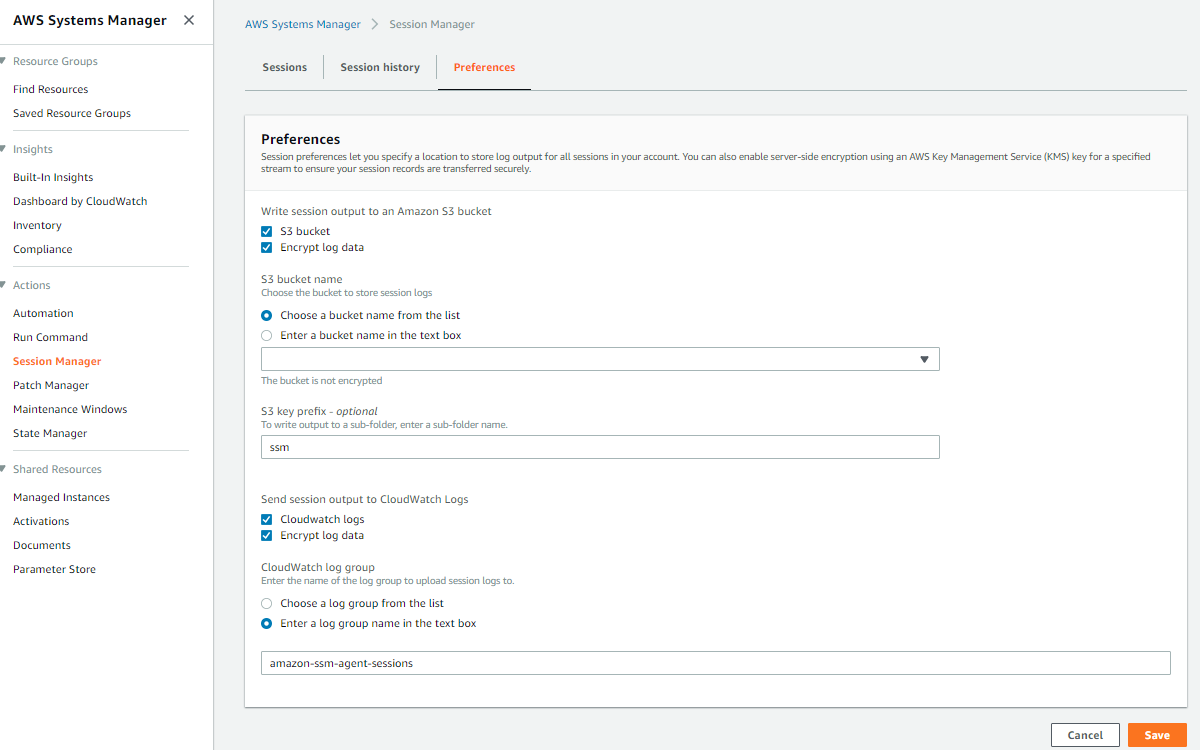
CloudWatch Logs
When you terminate a session, it'll go into the "Terminating" state in "Session History" tab. Once it's changed to "Terminated", the CloudWatch log will be saved:
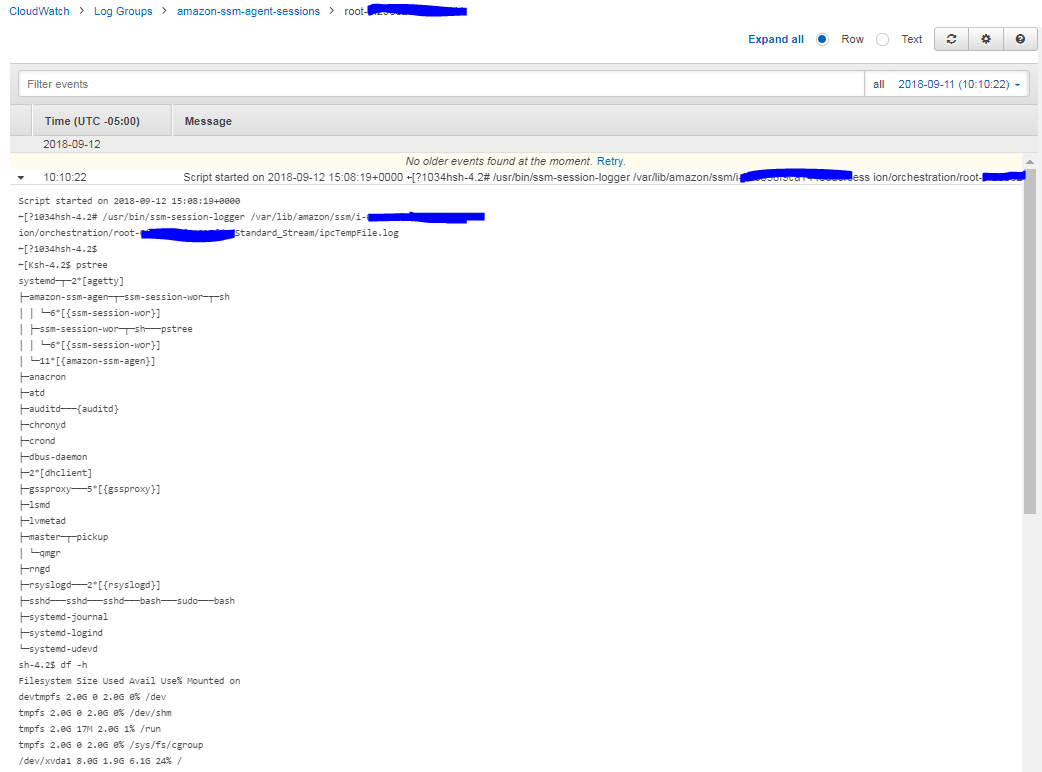
Session Log
Comments
comments powered by Disqus